aCropalypse - Why worry?
What is it?
aCropalypse (CVE-2023-28303) is a vulnerability affecting the screenshot editing tool found on Google Pixel devices since 2018, as well as Microsoft Snip & Sketch on Windows 10 and Snipping Tool on Windows 11. Although the vulnerability has been patched in both cases, if you have already shared or saved screenshots that were taken using these tools, it is important to be aware of the risk and take steps to protect your privacy.
The vulnerability affects the way an image is cropped or edited, such as redacting part of the image or covering personally identifiable information (PII) within the application with a black box, for example. In affected applications, when a file is redacted and saved, the original unedited image is still included within the edited file.
A telling way to identify this is by observing if the image size has not changed, which would be expected if parts of the image had been removed. The original image can be recovered and viewed with available software that exists online.
The original data, prior to redaction, isn’t visible in normal software - the redundant data would be ignored by conventional image viewing software, as the software would read the data to the point where the first file end marker is seen, ignoring any trailing data.
As this vulnerability has been present in the impacted systems for a while, historical images that have been created in this way and redacted for onward sharing (e.g., on social media, within documentation or similar) may be impacted and contain the unredacted, raw data.
Historically-created images may include sensitive information, such as PII, passwords, credit card information or technical details, which the creator of the image believes has been redacted from the image.
Although some social media sites and website CMS systems truncate uploaded images (probably mitigating the issue in many cases), images shared on social media sites via systems that don’t truncate images may be impacted.
Google and Microsoft have since published an emergency fix to rectify the issue. The fact that this bug was found in applications published by separate publishers raises concerns about how many applications may be affected by the same bug.
How do I know if my images are affected?
An inspection of the raw PNG files can indicate whether a redacted image is potentially impacted by the issue. You can use a hex editor to check for data after the IEND chunk:
- Open the PNG image in a hex editor of your choice.
- Look for the last four bytes of the file, which should be the IEND chunk signature "49 45 4e 44" in hexadecimal format.
- After the IEND signature, there should be no other data or bytes in the file. However, if you see data after the IEND chunk, it indicates that the PNG image file might be impacted.
Alternatively, you can use specialized tools like pngcheck, pnginfo, or pngnq to check for data after the IEND chunk. These tools can not only detect any additional data but also provide more detailed information about the PNG image, such as its color depth, compression type, and transparency settings.
The following is an example of an affected PNG file where “IEND”, which is used as an end-of-file marker, is found twice in the cropped version of the test image that was created with the Snipping Tool on Windows 11.
First IEND found with the original data following it:
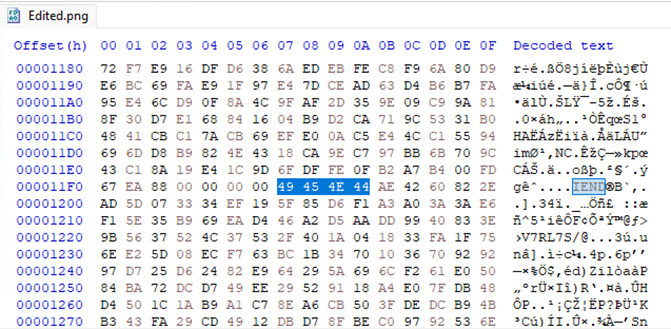
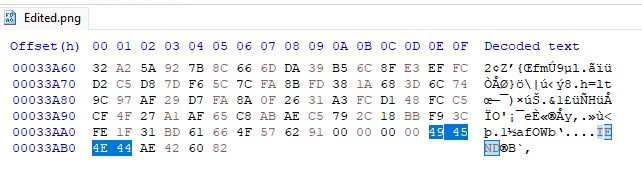
The end of the file has an expected IEND:
To use pngcheck to check for data after the IEND chunk of a PNG image, follow these steps:
- Open the command prompt or terminal on your system.
- Navigate to the directory where the PNG image is located using the "cd" command.
- Type the following command: pngcheck -v <filename.png>
The "-v" option in the command tells pngcheck to display detailed information about the PNG image. If there is any data after the IEND chunk, pngcheck will display an error message indicating that the file is corrupted or has been tampered with.
Here's an example of what the output might look like if there is data after the IEND chunk:
$ pngcheck -v example.png File: example.png (1582 bytes) invalid chunk length - this is not a PNG file? After IEND: 11 bytes ERROR: example.png
A quick Python script to check all files in a directory is below:
import os
import subprocess
# Define the directory path where the PNG files are located
dir_path = "path/to/directory"
# Get all PNG files in the directory
png_files = [f for f in os.listdir(dir_path) if f.endswith('.png')]
# Loop through each PNG file and check for data after the IEND chunk
for png_file in png_files:
# Construct the full file path
file_path = os.path.join(dir_path, png_file)
# Use pngcheck to check for data after the IEND chunk
output = subprocess.check_output(["pngcheck", "-v", file_path])
# Check if there is any data after the IEND chunk
if b'After IEND' in output:
print(f"File {png_file} has data after the IEND chunk.")
else:
print(f"File {png_file} is OK.")How worried should I be?
In terms of risk management, aCropalypse presents some real challenges – the patch prevents data from being exposed in redacted screenshots created from now on, but files shared with external parties or untrusted individuals over the years might potentially be impacted.
Given the widespread use of image sharing in personal and business life, it is likely to be extremely difficult for organisations to identify the overall risk posed by this issue.
Companies may have to take steps to establish if they are affected and assess the risk and contain further breaches. This may include but not be limited to checking historical documents and images shared on various websites, platforms and via other mechanisms to identify whether they are affected. Mapping where image redaction has been applied as a control to declassify or anonymise data is likely an important first step.
It’s likely that the after-effects of this weakness may be with us for some time, and that the worst impacts of this vulnerability - potentially in terms of ‘redacted’ information used in future data breaches, or extortion of companies or individuals over exposed data - are still to be felt.
Improve your security
Our experienced team will identify and address your most critical information security concerns.