One Identity Secure Password Extension Privilege Escalation (CVE-2025-27582)
What is One Identity Secure Password Extension?
A key component of One Identity's Password Manager, the Secure Password Extension provides users with self-service password reset capabilities from a locked workstation. It includes a kiosk-style browser that allows users to interact with the Password Self-Service site without logging in. This is intended to help legitimate users regain access to their accounts while maintaining security.
However, as we discovered, this feature also introduces an unintended attack surface—one that can be exploited to bypass security restrictions and escalate privileges.
Technical Breakdown: How the Exploit Works
Step 1: Bypassing the Security Hardening Mechanism
The Password Self-Service site runs in a restricted kiosk browser, which attempts to prevent certain privileged actions. One of these restrictions is the override of the window.print() function, preventing users from launching the print dialog from within the secure session:
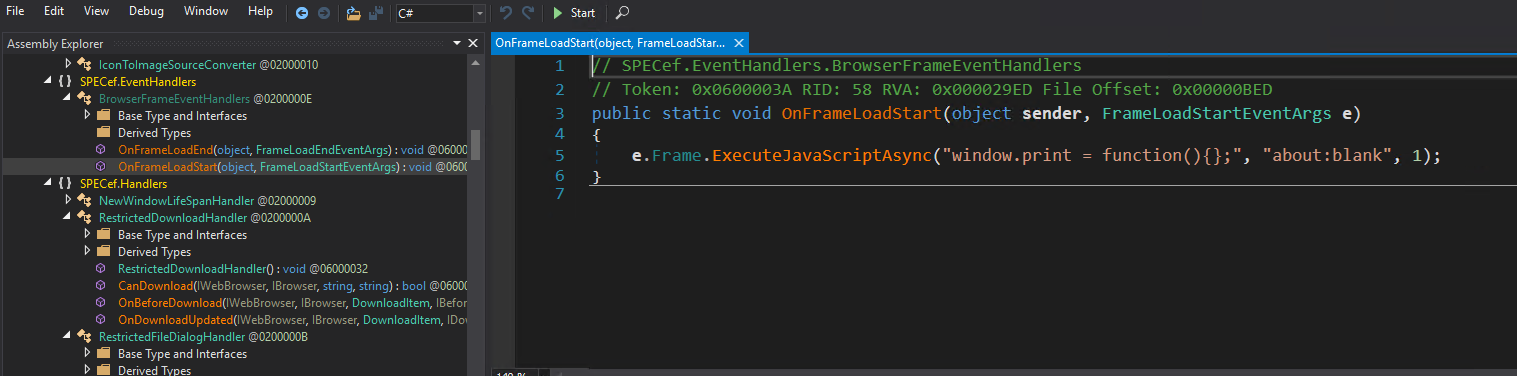
However, this security measure can be bypassed using the following steps:
- Lock the workstation or access an unlocked machine where the Password Self-Service feature is enabled.
- Open the Password Self-Service site from the lock screen.
- Use the “Help” function to navigate to an attacker-controlled website.
At this point, the attacker has control over the web content displayed within the kiosk browser.
Step 2: Reintroducing the Print Function
By hosting a malicious webpage, the attacker can inject JavaScript to restore and invoke the original window.print() function, which was previously restricted. The following script accomplishes this:
window.onload = function() {
let iframe = document.createElement("iframe");
document.body.appendChild(iframe);
window.print = iframe.contentWindow.print;
window.print();
};Once executed, this re-enables the print function, triggering a SYSTEM-privileged print dialog.
Step 3: Escalating to SYSTEM
From the print dialog, an attacker can exploit standard Windows functionality:
- Selecting Print to PDF allows access to a Save As dialog, which can be used to navigate the filesystem.
- Selecting Add Printer can open additional SYSTEM-level dialogs.
At this stage, the attacker can spawn a SYSTEM-privileged command prompt, gaining full control over the affected machine.
Impact: Why This Matters
This vulnerability enables a local attacker with access to a locked workstation to escalate privileges to SYSTEM, effectively compromising the entire device.
With SYSTEM privileges, an attacker can:
- Install malware or backdoors
- Modify system settings
- Extract sensitive credentials
- Disable security controls
Mitigation & Recommendations
We have responsibly disclosed the issue to One Identity, and we strongly recommend organisations using Password Manager take the following precautions:
- Restrict access to the Help function within the Password Self-Service kiosk, or at least ensure it is not possible to navigate away from the intended help website.
- Apply security updates provided by One Identity - https://support.oneidentity.com/password-manager/5.14.4/download-new-releases.
While this vulnerability requires local access, its ease of exploitation makes it a serious security concern for organisations relying on One Identity’s Password Management solution.
Affected Versions
- 5.14.3 and earlier
Vendor Response
"We appreciate the responsible disclosure by Cyberis and are grateful for the patience of our customers. Our validation process in this instance, particularly the rigorous internal testing, resulted in a longer-than-ideal gap between initial disclosure and patch availability."
"Protecting our customers remains our top priority, and we are committed to refining our processes to deliver fixes more quickly while maintaining the highest standards of security. To our knowledge, no customers were impacted by this vulnerability."
— Tibor Vida, Director of Software Engineering, One Identity
Vendor contact timeline
- 2025-02-28: Contacted vendor through https://support.oneidentity.com/contact-us/report-security-vulnerability
- 2025-03-01: CVE requested via MITRE
- 2025-03-03: CVE-2025-27582 assigned
- 2025-03-04: One Identity advise of two potential mitigations for the vulnerability
- 2025-07-08: Patch released- https://support.oneidentity.com/password-manager/5.14.4/download-new-releases
- 2025-07-11: Vendor response received
- 2025-07-14: Blog post published and Mitre informed of public disclosure
Improve your security
Our experienced team will identify and address your most critical information security concerns.